David Stang
Seven Locks Software, Inc.
This paper provides an overview of the computer virus problem. It was developed by Seven Locks Software, as part of our public education program.
Some of the content of this paper concerns virus prevalence, and was drawn from the best, most recent study of the subject, the International Computer Security Association's 1997 Computer Virus Prevalence Study. Seven Locks Software sponsored this survey of 300 sites representing over 700,000 desktop computers, and is proud to be a vendor member of the ICSA's Anti-virus Product Developer Consortium.
A virus is a piece of software designed and written to make additional copies of itself and spread from location to location, typically without user knowledge or permission. Thus a virus is "self-reproducing code." Many viruses go beyond "quiet" operation, and are coded to avoid detection by the most common methods used. Such stealth qualities are now found in both viruses infecting files ("file viruses") and those infecting boot areas ("boot viruses").
There are computer viruses that were written specifically for operating systems (DOS, Windows 3.x, Windows 95, Windows NT, OS/2, and UNIX) and specific machines (Intel CPU machines, Amiga, Mac, and Atari.). The most common viruses today are operating system independent: they will run under any operating system if other conditions are met.
The largest category of viruses, however, is not the most prevalent. For years, the greatest number of different viruses have been file viruses - viruses which infected programs, such as DOS COM and EXE files. Such viruses never accounted for the greatest number of infections - back in the days of DOS, boot viruses were more common than file viruses - but have always accounted for the biggest headache for vendors of anti-virus products. The sheer number of file viruses, and their continued high rate of emergence, has always kept developers busy.
Like biological viruses, computer viruses are very small, and have one characteristic of life: the ability to reproduce.
Viruses, by definition, add their code to your system in such a way that when the infected part of the system executes, the virus does too: The exact mechanism of attachment depends on whether the virus is a boot virus, file virus, macro virus, etc.[ The "companion virus" attaches to the file system. This type of virus is rare, and will not be discussed here.]
Some viruses display symptoms, and some cause damage to files in a system they have infected. But neither symptoms nor damage are essential in the definition of a virus. A non-damaging virus is still a virus, not a prank. Some viruses cause damage, but not all do. Some display obvious symptoms, such as messages, but the most common are usually difficult to detect, and largely free of obvious symptoms.
There are no "good" viruses, simply because virus is code that was not intentionally installed by the user. Users must be able to control their computers, and that requires that they have the power to install and remove software; that no software is installed, modified, or removed without their knowledge and permission. A virus is surreptitiously self-installed. It may modify other software in the system without user awareness, and removal can be difficult and costly.
Many viruses cause intentional damage. But many more cause damage that may not have been intended by the virus author. For instance, when a virus finds itself in a very different environment than that for which it was written, a non-destructive virus can suddenly become very destructive. A good case in point is the boot virus: while a particular boot virus might not contain any code to damage computers running Windows NT, booting an NT machine with such a virus is likely to be the end of the system.
Even if a virus causes no direct damage to your computer, your inexperience with viruses can mean that damage occurs during the removal process. Many organizations have shredded floppies, deleted files, and done low-level formats of hard disks in their efforts to remove viruses. Even when removal is done perfectly, with no damage to the infected system or files, it is not normally done when the machine is first infected, and the virus in that machine has had a few weeks to spread. The social costs of infection include a loss of reputation and good will.
We have said that not all viruses cause damage. Some do nothing but make copies of themselves. So is this a problem?
Our answer is Yes. All viruses are problems. One reason a virus causes problems is simply that some effort must be expended to detect and remove it. The average incident [a computer virus incident here is a virus encounter where a minimum of 25 PCs, diskettes, or files were infected by the same virus at approximately the same time.] may cost us over $8,000 in a large organization, as may be seen in the table below.[From NCSA 1997 Virus Prevalence Survey.]
Table 1. Cost of Incidents, 1997
| Measure | Cost |
|---|---|
| Server Downtime | 40 minutes |
| Time to Recovery | 44 hours |
| Person Days Lost | 22 |
| Financial Cost | $8,366 |
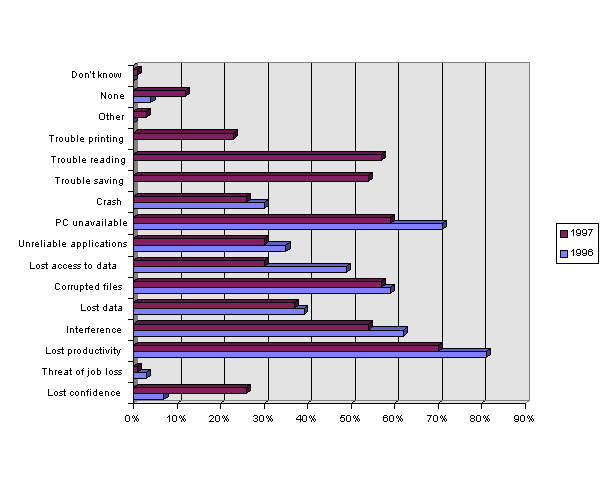
The effects of viruses are not merely in machine downtime or recovery time. The greatest problem that computer viruses cause is related to loss of productivity and includes: PCs unavailable to users, loss of access to data, unreliable applications, and system crashes. Many users report corruption of PCs, applications, and data occurred via: screen message, interference, or lockup; corrupted files, lost data, and system crashes. In addition, viruses impact our confidence in our computers, and our trust of the procedures and policies we have designed to protect us. Some effects are shown in Table 2. Effects of Viruses, 1996-1997 and Figure 1. Effects of Viruses, 1996-1997.[ From NCSA 1997 Virus Prevalence Survey.]
Table 2. Effects of Viruses, 1996-1997
| 1996 | 1997 | |
| Loss of user confidence in the system | 7% | 26% |
| Threat of someone losing their job | 3% | 1% |
| Loss of productivity (machine, applications or data not available for some time) | 81% | 70% |
| Screen message, interference, or lockup | 62% | 54% |
| Lost data | 39% | 37% |
| Corrupted files | 59% | 57% |
| Loss of access to data (ie. on Server, Host, Mainframe, etc.) | 49% | 30% |
| Unreliable applications | 35% | 30% |
| PC was unavailable to the user | 71% | 59% |
| System Crash | 30% | 26% |
| Other (specify) | 0% | 3% |
| None | 4% | 12% |
| Don't know | 0% | 1% |
Figure 1. Effects of Viruses, 1996-1997
No. Virus creation is at an all-time high. Viruses are spreading more easily than ever. Your chance of infection is higher than ever.
There are two specific aspects of the problem that should be considered separately:
For a decade, computer viruses have caused problems for users and organizations. During this period, a number of vendors have developed products to address the virus problem, but the problem has only grown worse.
At the start of 1987, there were a total of six different viruses. Today there are "close to 12,000" according to one trusted source. [Virus Bulletin, "Pawn to King-four" July, 1997. P.2] In that 10 year period, the number of viruses doubled 11 and a half times., or every 10.5 months. If this doubling rate holds, there will be 24,000 viruses next year.
The approaches which vendors have used in the past are challenged by this immense rate of emergence of new viruses. If 12,000 viruses are created in the next 10.5 months, vendors will have to develop detection and removal instructions for 1,142 viruses a month, a rate of about 6 viruses per hour for every normal working hour. Since developing manual creation of detection and removal instructions can take as long as one or two working days for difficult viruses, either a large staff or an automated virus analysis system will be required of all successful vendors if they are to keep up.
The rate of emergence of new macro viruses suggests that these numbers are conservative. The number of macro viruses has gone from 1 in August 1995 to 42 in August 1996 to 1,000 in June 1997 [Virus Bulletin, "1000 Macro Virus Mark Passed" July, 1997. P. 3], a doubling rate of 2 months, rather than 10.5 months. This is primarily because macro viruses are much easier to create than boot and file viruses. But creating detection and removal instructions is just as difficult for macro viruses as it is for other kinds.
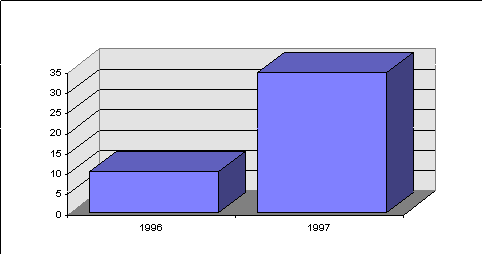
The probability of infection has increased considerably in the last decade, and continues to rise. Today, the probability of infection is at about 35 infected computers per 1,000 per month. Put another way, 42% of computers are likely to become infected in the next 12 months. This infection rate is about 3.5 times as high as a year ago, when the rate was about 10.3 computers per 1000 per month. There is little doubt that the virus problem is growing, and at a considerable rate. (See Figure 2. Infections Per 1,000 Computers Per Month, 1996-1997 [From NCSA 1997 Virus Prevalence Survey.]
Figure 2. Infections Per 1,000 Computers Per Month, 1996-1997
One survey [NCSA 1997 Virus Prevalence Survey.] finds that only 73% of respondent desktop machines have an anti-virus product installed. According to a poll reported in Virus Bulletin [Virus Bulletin], "and Still too Few Precautions" July, 1997. P. 3] more than 50% of users do not update their anti-virus software on a monthly or more frequent basis. Fifty-two percent of respondents were unaware that their anti-virus product vendor offered updates free to its customers. This suggests that some part of the problem of virus prevalence might be blamed on user behavior and knowledge.
In short, despite whatever quality improvements vendors might have made in their products, the increased number and prevalence of viruses indicates that the problem is growing worse.
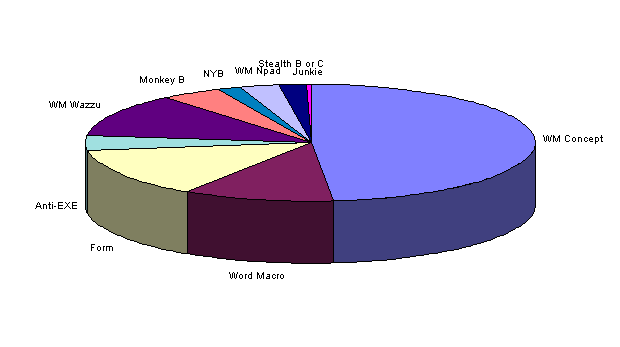
Today, our most common virus infections are of Word macro viruses. During 1997 one virus, the Word.Concept virus (also known as WM.Concept and Prank), infected one-half (49%) of survey sites (compared with only 12% in the prior year). This year's survey witnessed the remarkable growth of this family, with macro viruses of all sorts accounting for 80% of infections reported (compared with 41% in the prior year). Word.Concept was first distributed in July, 1995, and has experienced the most rapid growth in prevalence of any virus yet. Table 3. Which viruses have affected your group's PCs during 1997? and Figure 3. Relative Dominance of Top Ten Viruses, 1997 show the most common viruses reported in the past 12 months. [NCSA 1997 Virus Prevalence Survey.]
Table 3. Which viruses have affected your group's PCs during 1997?
| Virus | Percent Reporting |
|---|---|
| WelcomB | 1.68% |
| Word Macro | 15.10% |
| Word Macro Concept | 34.23% |
| Word Macro Npad | 4.36% |
| Word Macro Wazzu | 19.13% |
| Word Macro MDMA | 2.68% |
| Word Macro Colors | 2.01% |
| Excel Macro | 0.67% |
| XM Laroux | 1.01% |
| Other (SPECIFY) | 25.17% |
| None | 5.37% |
| Don't know | 8.72% |
| Refused | 0.34% |
Figure 3. Relative Dominance of Top Ten Viruses, 1997
Nearly all viruses shown in Figure 4 have become more prevalent over the approximately one year covered by this data (note: accounting for the survey biases might dampen this effect). Only Junkie, from these top ten, appears to be in decline. The greatest growth rates are of the top macro viruses, such as WM.Concept and WM.Wazzu.
Figure 4. Infections per Month per 1,000 Computers, Top Ten Viruses
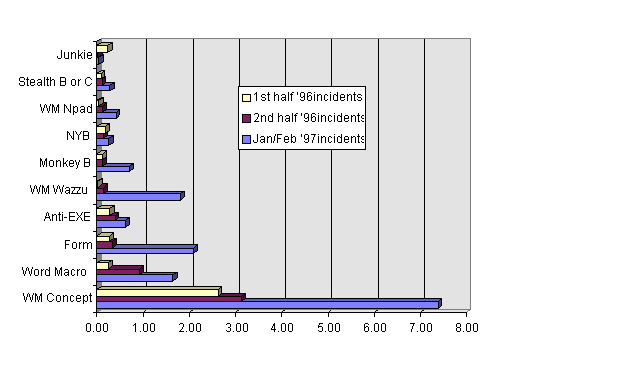
Of the top ten viruses, seven are at least five years old (NATAS, NYB, and WM.Concept were approximately 3, 3 and 1.6 years old at the time of this survey). Until WM.Concept, Natas and NYB, were apparently "growing" the fastest. By far, the rate of growth of WM.Concept is the fastest of any virus ever observed to infect computers of the general public. There are several reasons for its apparent rapid growth:
We should note that a virus which appears to be in decline may actually be increasing in prevalence. If a user is infected with an older virus that is easily dispatched with the product on hand, that user is likely to kill the virus without reporting it to management. If the virus is contained because of the effectiveness of anti-virus products, it is not likely to be remembered, and thus not likely to be reported to our survey researchers. It is those viruses which cause unpleasant experiences, data loss, massive infection, and which prove difficult to remove that are most likely to be recorded.
The NCSA 1997 Virus Prevalence Survey asked three questions concerning which viruses affected the group:
5a. Which viruses have affected your group's PCs during 1997? How many times? (do not read the list)
5b. Which viruses affected your group's PCs during the second half of 1996 (July-December)? How many times?
5c. Which viruses affected your group's PCs during the first half of 1996 (January-June)? How many times?
We have tabulated answers in two forms: the percentage of respondents having an incident with the virus, and the total number of infected machines (sum of "how many times" question across respondents.)
Table 4. Most Commonly Found: Percent of Organizations Infected
| Virus | Jan/Feb '97 | 2nd half of '96 | 1st half of '96 |
|---|---|---|---|
| Anti-CMOS | 10% | 12% | 8% |
| Anti-EXE | 18% | 16% | 12% |
| Form | 16% | 18% | 16% |
| Green Caterpillar | <1% | 0% | 0% |
| Jumper | 0% | <1% | 0% |
| Junkie | 2% | 2% | 1% |
| Michelangelo | 3% | 2% | 3% |
| Monkey B | 17% | 15% | 12% |
| NATAS | <1% | 1% | 1% |
| NYB | 10% | 7% | 5% |
| One Half | <1% | <1% | 0% |
| Parity Boot | 1% | 1% | <1% |
| Ripper | 3% | 4% | 3% |
| Stealth B or C | 14% | 13% | 10% |
| Stoned (Monkey Empire) | 13% | 14% | 15% |
| WelcomB | 2% | 2% | 1% |
| Word Macro | 15% | 12% | 7% |
| WM Concept | 34% | 31% | 19% |
| WM Npad | 4% | 3% | 1% |
| WM Wazzu | 19% | 10% | 5% |
| WM MDMA | 3% | 2% | <1% |
| WM Colors | 6% | <1% | 0% |
| Excel Macro | 1% | 1% | <1% |
| XM Laroux | 1% | <1% | <1% |
| XM Sofa | 0% | 0% | 0% |
| Other (specify) | 25% | 19% | 13% |
| None | 5% | 2% | 3% |
| Don't know | 9% | 22% | 39% |
| Refused | <1% | <1% | <1% |
Table 5. presents an estimated total number of machines infected throughout the survey. Thus if only two respondents reported this virus at all, each reporting 100 infected machines in the time period, the number "200" would be presented in the table. As such, this table doesn't show what percentage of organizations were infected with the virus, or what percentage of machines within the average organization were infected. But it does provide a sensitive measure of the success of a virus in infecting machines.
Table 5. Viruses Most Commonly Found: Total Infections
| Virus | Jan/Feb '97 | 2nd half '96 | 1st half '96 | Total |
|---|---|---|---|---|
| WM Concept | 10750 | 13662 | 11481 | 35893 |
| Word Macro | 2392 | 3990 | 1104 | 7486 |
| Form | 3048 | 1478 | 1187 | 5713 |
| Anti-EXE | 906 | 1721 | 1240 | 3867 |
| WM Wazzu | 2632 | 659 | 135 | 3426 |
| Monkey B | 1021 | 512 | 497 | 2030 |
| NYB | 390 | 667 | 839 | 1896 |
| WM Npad | 602 | 540 | 202 | 1344 |
| Stealth B or C | 414 | 481 | 377 | 1272 |
| Junkie | 67 | 108 | 1040 | 1215 |
| Stoned (Monkey Empire) | 167 | 516 | 353 | 1036 |
| Anti-CMOS | 230 | 422 | 290 | 942 |
| Excel Macro | 100 | 70 | 50 | 220 |
| WM MDMA | 196 | 6 | 0 | 202 |
| Michelangelo | 17 | 45 | 128 | 190 |
| Ripper | 32 | 66 | 58 | 156 |
| WelcomB | 20 | 101 | 35 | 156 |
| NATAS | 0 | 79 | 23 | 102 |
| One Half | 11 | 10 | 0 | 21 |
| WM Colors | 7 | 5 | 0 | 12 |
| XM Laroux | 10 | 2 | 0 | 12 |
| Jumper | 0 | 10 | 0 | 10 |
| Parity Boot | 4 | 2 | 0 | 6 |
| Green Caterpillar | 1 | 0 | 0 | 1 |
| XM Sofa | 0 | 0 | 0 | 0 |
Several observations on this table:
Figure 5. Relative Prevalence of Top Ten Viruses
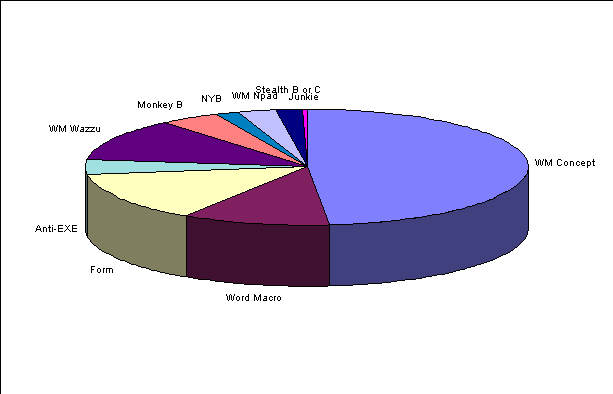
Much has been made of the phrase "in the wild." The list of viruses commonly believed to be "in the wild" - sometimes found on the desktop computers in homes and offices like yours - is a short list. Some vendors boast that they detect all viruses "in the wild", whereas they really detect viruses found on the "in the wild" list.
There are many such problems with this approach. A virus can be written and distributed today, and infect your machine tomorrow. Whether it ever appears on an in-the-wild list or not is a matter of chance, but it certainly won't be on the list if it is quite new.
In the NCSA survey, respondents were asked to name other viruses found in their organization in the past year. Many were named. Few of these appear on the official "wild list." Many of these additional viruses are macro viruses. 15 years/Espejo/Esto te, Aloha, Anti-Alias, Anti-OC, Arachina, B-1, Barrotes, BLU, BOOT B, Boot Virus, Bupt/WelcomB, Cascade, D 1, Da'Boys, Dr. White, Dragon, Exabyte.3, EXEC, Form.A, Frankenstein, Fu_Manchu, Int 10, J&M, Jerusalem, Jerusalem.Mummy, Joshi, Junkie, Leandro, Meat Grinder, MICROSOFT, Mirrox General 1, Music_Bug, Natas, NYB, PacMan, Read IOSys, Sampo, Stealth.B-1, Stealth.Boot.H, Stoned, Stoned.Angelina, Stoned.Bloomington/NoInt, Stoned.Empire.Monkey, Stoned.No_Int, Tai-Pan.666/Doom2Death, Telecom.Boot, Tentacle, Trojan Horse, Typen, Urkel, V-Sign, WM.Alien, WM.Bandung, WM.CAP, WM.Concept.A-F, WM.Divina, WM.DMV, WM.Imposter,WM.Indonesia, WM.Irish, WM.Johny, WM.Lunch.A, WM.NOP, WM.Npad, WM.Nuclear, WM.Rapi, WM.ShowOff, WM.Wazzu.A-F, WM.Wazzu.C, WordPerfect virus.
While it is important for you to choose protection that can deal with everything listed on an "in the wild" list, you must recognize that your could just as easily get a virus not on the list; your product and vendor must take care of you whether or not the virus you get next is listed.
Knowledge of how viruses get into our computers is useful in deciding how to defend against viruses.
Diskettes and downloads account for the majority of our infections. Table 6. Sources of Infection, 1996-1997 and Figure 6. Infection Sources shows how survey respondents believed their machines had become infected. Note that respondents could choose more than one infection source for their most recent infection, so totals exceed 100%.
Table 6. Sources of Infection, 1996-1997
| Source | 1996 | 1997 |
|---|---|---|
| A diskette, sales demo or similar | 11% | 8.05% |
| A diskette, repair/service person | 3% | 3.36% |
| A diskette, LAN manager/supervisor | 1% | 2.68% |
| A diskette, shrink-wrapped software | 2% | 4.36% |
| A diskette, malicious person intentionally planted | 0% | 1.01% |
| A diskette, brought from someone's home | 36% | 42.28% |
| A diskette, other | 21% | 26.51% |
| On a distribution CD | 0% | 0.67% |
| A download from BBS, AOL, CompuServe, Internet | 10% | 16.11% |
| Other download (terminal emulation, client server) | 2% | 2.35% |
| Via e-mail as an attachment | 9% | 26.17% |
| Via an automated software distribution | 0% | 1.68% |
| While browsing on the World Wide Web | -- | 5.37% |
| Other | 0% | 5.03% |
| Don't know | 15% | 7% |
Figure 6. Infection Sources
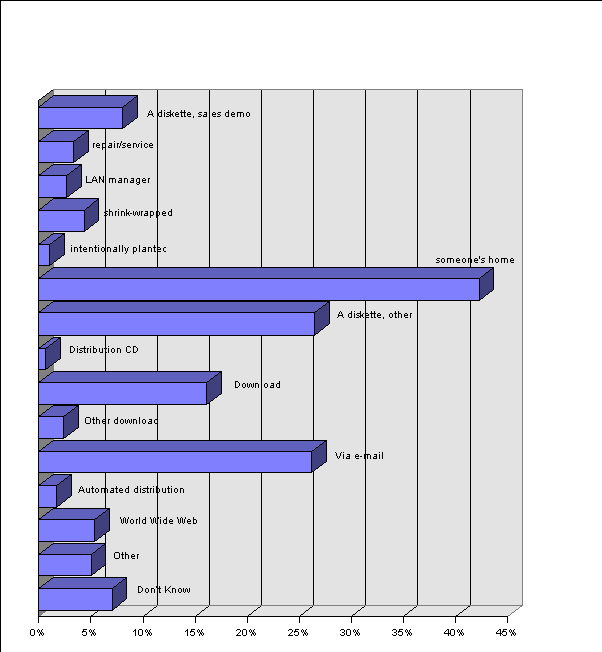
It is not surprising that diskettes predominate as a vector for infection, since nine out of the top ten most prevalent viruses and 17 out of the top 20 were boot viruses and could not travel by any other means. However, in the 1991 NCSA-Dataquest survey, the proportion of diskettes was even larger (87%), download sources were slightly lower, and e-mail attachment was not mentioned as a source or possible source.
Macro Virus Also Travels by E-mail and the Net - All viruses can, theoretically, be transferred by diskette, by e-mail, or by download.[ A boot virus can be transferred by e-mail if a "dropper" is attached to the e-mail. When the attachment is run, the dropper can insert the boot virus in the appropriate sectors of the drive. Such transfer of boot viruses is extremely rare. Similarly, a boot virus may be downloaded if the file downloaded is a dropper. The spread of boot viruses via droppers via download is extremely rare.] though all viruses can travel by diskette, only executable file-type and macro viruses can possibly travel by download or e-mail attachment. We looked at the top viruses to determine how they got to the organization. As may be seen in Table 7 and Figure 7, macro viruses are most likely to enter an organization via e-mail attachments, whereas boot viruses most often come via diskette. The home remains a common source of virus infection in offices.
Table 7. Sources of Infection, Boot and Macro Viruses, 1997.
| Boot | Macro | |
|---|---|---|
| A diskette, sales demo or similar | 2% | 3% |
| A diskette, repair/service person | 7% | 1% |
| A diskette, LAN manager/supervisor | 0% | 1% |
| A diskette, shrink-wrapped software | 2% | 3% |
| A diskette, malicious person intentionally planted it | 2% | 0% |
| A diskette, brought from someone's home | 26% | 17% |
| A diskette, other | 23% | 12% |
| On a distribution CD | 0% | 0% |
| A download from BBS, AOL, CompuServe, Internet, etc. | 9% | 7% |
| Other download (terminal emulation, client server) | 2% | 2% |
| Via e-mail as an attachment | 2% | 36% |
| Via an automated software distribution | 0% | 0% |
| While browsing on the World Wide Web | 5% | 5% |
| Other | 7% | 2% |
| Don't Know | 12% | 9% |
Figure 7. Sources of Infection, Boot and Macro Viruses, 1997.
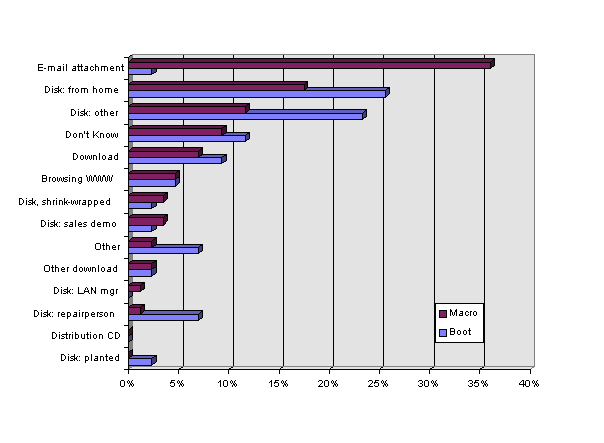
Table 8 shows the analysis from the 1996 survey. In both surveys, e-mail was especially important as a transmission vehicle for macro viruses. The speed and international quality of e-mail will likely continue to contribute to the rapid spread of new and old macro viruses in coming years.
Table 8. Means of Infection Summary, 1996 Survey
| Download from BBS, AOL, C/S, Internet or Other | ||
|---|---|---|
| All Viruses Except Word.concept | 7.7% | 11.7% |
| All Viruses | 8.8% | 11.5% |
| Word.concept Encounters | 21.5% | 17.8% |
| Word.concept Incidents | 30.5% | 14.2% |
In planning your own defense, you might benefit from knowing how others defend their desktop machines.
Respondents in the NCSA Virus Prevalence Survey were asked to estimate the number of PCs which were protected by each of several methods: Respondents could choose more than one answer. Results are shown below for both the percentage of respondents using a method, and the number of machines protected by the method. If you add up the number of PCs protected by various methods, you find that 1,430,256 machines are protected by the methods; with only 728,798 machines represented in the study, we can conclude that each machine averages two protection methods.
Table 9. Desktop Virus Protection Methods Used
| Protection | % Respondents | # of PCs |
|---|---|---|
| Users check diskettes and downloads for viruses. | 64% | 320,268 |
| Anti-virus software scans hard drive for viruses every boot-up | 68% | 402,598 |
| Anti-virus software scans hard drive for viruses every login | 39% | 194,526 |
| Anti-virus software scans hard drive for viruses full time in the background | 60% | 289,740 |
| Other periodic anti-virus detection on the desktop | 41% | 132,770 |
| Other full-time anti-virus detection on the desktop | 20% | 58,881 |
| Other (specify) | 5% | 31,473 |
| None | 1% | |
| Don't know | <1% |
A closer look at desktop protection methods finds that only 16% of respondents used only one of the above methods of protection, 19% used two, and 32% used three. The distribution of respondents on this question, showing the number of methods used, is provided in the table below.
Table 10. Number of Desktop Protection Methods Used
| 1 | 2 | 3 | 4 | 5 | 6 |
|---|---|---|---|---|---|
| 16% | 19% | 32% | 19% | 11% | 3% |
The best prevention is a combination of changing your computing behavior and using an anti-virus product wisely:
The following are common terms used in discussions of anti-virus software: