Eric Filiol
INSTITUT NATIONAL DE RECHERCHE EN INFORMATIQUE ET EN AUTOMATIQUE
ISSN 0249-6399
January 2002
![[PS ]](../img/ps.gif) Download/Read the article (PS, 448K)
Download/Read the article (PS, 448K)
Theme 2 - Genie logiciel et calcul symbolique Projet Codes
Rapport de recherche n*4359 - Janvier 2002 - 15 pages
Abstract: This report presents a new class of techniques which allow either the attack of a computer or to catch the keys of a cryptosystem by using a pair of (or combined) viruses, one of them being hidden by the attacker in ciphertext. These techniques are valid for any operating system and can be effciently implemented in any programming language and for any operating system. In order to avoid detection, the viral infection is very limited and uses polymorphic techniques. Moreover the main virus erases itself after the payload action. The general structure of the two viruses is presented and the problem of protection against such attacks is onally envisaged.
Key-words: Computer security, applied cryptanalysis, symmetric cipher, ciphertext, computer viruses, steganography, PGP, AES.
(Resume : tsvp)
also Virology and Cryptology Lab, French Army Signals School, ESAT/DEASR/CSSI, 35998 Rennes, France, eoliol@esat.terre.defense.gouv.fr
* Projet Codes - Eric.Filiol@inria.fr
Unite de recherche INRIA Rocquencourt
Domaine de Voluceau, Rocquencourt, BP 105, 78153 LE CHESNAY Cedex (France) Telephone : 01 39 63 55 11 - International : +33 1 39 63 55 11
Telecopie : (33) 01 39 63 53 30 - International : +33 1 39 63 53 30
The recent evolution of modern symmetric cryptology has led to the widespread use of highly secure secret key cryptosystems. Among many examples (IDEA [12], GOST [8], Blowosh [18],...) the best ones are without doubt the different candidates proposed for the A.E.S [1], for the NESSIE project [16] or at CRYPTREC [5]. The same problem is encountered with highly secure steganography products (Outguess [17] and others [21]).
Despite frequent highly unrealistic claim of cryptanalysis, these cryptosystems may be considered as unbreakable for a very long time to come. Neither the brute force attack (exhaustive search on the key-space) nor the published mathematical or algorithmic analysis are likely to yield "operational, real-time" cryptanalysis for these ciphers in the next few years.
An FBI spokesman recently [4] acknowledged the fact that "encryption can pose potentially unsurmountable challenges to law enforcement...".
As an example, let us consider the case of the AES. Let us suppose that we use a deepcrack like computer allowing exhaustive key search of 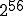 key in one second. Then brute force attack on the different AES version will:
key in one second. Then brute force attack on the different AES version will:
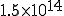 centuries for 128-bit keys.
centuries for 128-bit keys.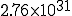 centuries for 192-bit keys.
centuries for 192-bit keys.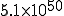 centuries for 256 bits keys.
centuries for 256 bits keys.The situation is quite different when considering another kind of cryptanalysis that the "operational men" call "applied cryptanalysis".
Definition 1 Applied cryptanalysis describes the set of all non mathematical means and techniques which aim at attacking a cryptosystem either on its implementation or on its everyday use in order to endanger its secret key thus allowing easy deciphering to the attacker.
With regards to this deonition, physical techniques such as timing attack [10] and power analysis [3, 11] are recent known examples. However these techniques nearly always require highly technical knowledge, costly hardware and the need to have physical access to the cryptosystem or at least to its implementation (e.g. smart card). Stealing cryptographic material may very likely provoke the complete change of the keys.
Human compromise of the secret key user or secret key theft are less well known but have been shown to be very effective during previous wars as spying history teaches us [9]. The main drawback of this approach comes from the fact that it is both risky and incautious. Moreover, close contact with the user is always directly or indirectly necessary. Once again compromission of the keys may be, with a good probablility, detected thus leading to the replacement of the keys.
Another technique is to have access to the hard disk when considering encryption softwares and to make it "speak"; in most cases, cryptographic softwares are so badly implemented that swap mechanism between processeur and hard disk nearly all the time, (unprotected) secret keys may be present on the hard disk for a very long time. A simple analysis of the hard disk will ond them. Of course, the major drawback is to have physical access to the target computer, and the "victim" will no longer use its keys.
A more interesting, operational approach consists of using "infecting softwares". One of the orst known attempt is the Caligula virus [20] but it was totally ineffcient, since this macro virus stole encrypted, thus useless, secret key of PGP. Recently [4] the FBI has acknowledged the use of Magic Lantern Technology in a broader project called "Cyber Knight". The aim is to capture the user's secret keys by installing Trojan-like powerful software over the Internet which will perform eavesdropping of the target computer keyboard buffer. Such an approach has been very recently observed with the new worm BadTrans [20] which essentially steals passwords by keyboard buffer eavesdropping too. Unfortunately for the attacker, due to their high replicating power, worms are bound to be detected very quickly. in the other hand viruses embedding many functionalities are generally of large size. It implies that their infectious capabilities are rather limited and moreover they are liable to be easily detected due to their size.
The aim of this paper is to present a new, effcient technique of applied cryptanalysis using other less-known infecting malwares: binary (combined) computer viruses. In particular, we present an operational approach which effectively allowed us to remotely get the secret key of a target user, during the various experiments we conducted, without detection by recent anti-virus softwares and of course the "target". In our experiments we considered several now very famous "unbreakable" cryptosystems.
Each time we managed to get the user's secret key very easily. The main trick was to use the ciphertext as a "vehicle" for our attack (but other variants are now being implemented: e-mail attachement, sniffer module,...).
Combined (or pairs of) viruses have been used in this attack (i.e. two computer viruses which combine their respective payload to obtain a given onal effect). For details on these little known computer viruses see [7]). One resident, polymorphic, stealth virus detects the presence of a second virus, hidden by the attacker in the ciphertext, and launches it. This latter then conducts the attack itself by selectively infecting cryptosystems executables and allowing the onal secret keys to escape. Just after its payload action the second virus will disinfect itself, leaving no trail of its presence. Moreover it attributes polymorphic and stealth properties to the orst virus.
The main interest of two complementary viruses instead of one (which could itself steal the secret keys), is that infection is broken in two independent parts which never simultaneously occur. As a result, we always deal through the different steps of the attacks with small thus stealthier viruses. A virus alone could not work so effciently and with such stealth capabilities.
Thus physical access to the host computer is no longer necessary. The attack is very easy to conduct and required very limited means. Moreover it has been made completely stealthy in order to avoid detection. Otherwise it would inevitably induce the user to change their secret keys.
The paper is organised as follows. Section 2 presents the general overview of these attacks. In particuliar we deone precisely the operational context. In Section 3 the orst infection level is presented while Section 4 describes the second level of infection. Section 5 details the different possible attacks themselves which essentially aims at attacking the cryptosystem and at "key release". The case of a simple computer attack with a Trojan horse is presented as well. In Section 6 we try to envisage possible protection against these attacks.
Warning and Claim : the purpose of this paper is purely research and is not in any way to promote, help or encourage such attacks or the use of viruses. Our motivation is to draw the attention of security specialists to new attacks which have been proved dramatically effcient. We emphasise the fact that such attacks, as well as use of computer viruses, are harshly punished by the law in most of countries.
We now present the general description of this family of attacks before entering into details in Sections 3, 4 and 5 and then the operational condition of our experiments.
We will not recall the deonition of a virus and basic concepts on viruses that are used in this paper. Readers keen to know more will easily ond out more in all common handbooks dealing with computer viruses and particularly in [7, 13].
Let us consider the following setting for our attack. Two users, Alice and Bob, communicate via encrypted files. To do so they both use a strong symmetric cryptosystem denoted S. Alice orst encrypts her plaintext P with secret key K, producing ciphertext C which is onally sent to Bob.
The attacker Charlie intercepts C and just appends a virus executable file V2 which will perform the attack on Bob's computer. Finally (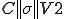 )1 is sent to Bob after insertion of a signature
)1 is sent to Bob after insertion of a signature 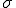 . Here the word "signature" must be taken in its viral meaning that is to say a caracteristic string allowing viral detection (viral signature). When dealing with the concept of signature as used in cryptography, we will use the term "cryptographic signature" in this paper. Thus possible confusion between these two concepts will be avoided.
. Here the word "signature" must be taken in its viral meaning that is to say a caracteristic string allowing viral detection (viral signature). When dealing with the concept of signature as used in cryptography, we will use the term "cryptographic signature" in this paper. Thus possible confusion between these two concepts will be avoided.
Thus at a preliminary stage, Bob's computer has been infected by another virus V1 which is of a resident, polymorphic, stealth kind2. It is designed in such a way that each time Bob switches his computer on, virus V1 is launched and stays resident. Its role is to permanently look for a received file with V2 appended to it. When found and identioed through signature ö, V2 is launched by V1, and ciphertext integrity is restored, that is to say V2 and signature ö are removed from the ciphertext.
When launched V2 looks for cryptosystem executables S to infect and then do so. As a consequence V2 is a very low-infecting, victim-specioc virus (generally one executable depending on to the victim's computer). When deciphering the ciphertext Bob in fact orst launches virus V2 which performs the following tasks:
If Bob performs other decipherings before enciphering, V2 in the same way will capture the key and store it with the previous ones if different from them. Let us suppose that secret keys K;K' have been previously stored by V2. When Bob performs a orst enciphering (that is to say orst enciphering after infection by V2) with secret key K'', V2 once again is orst launched and performs the following tasks:
The file (C'; K;K'; K'') is sent by Bob. Charlie again intercepts this file and get the concealed keys K;K'; K''. The attack is completed. Remark.- Since V1 is still present and remains undetected the attack can be conducted as often as required by the attacker.
Different variants of this attack scenario have been conducted with several, different contexts, the context being deoned as a set of the following elements:
Our aim is not to tarnish commercial products which are nonetheless rather good and useful products against known viruses. The interest and the force of our attack is to use very specioc, low-infecting viruses which use completely new and unpublished polymorphic techniques. None of the AV products we tested has been effcient at detecting viruses V1 and V2. This unfortunately comes from a "natural" limitation in current state-of-the-art AV technology.
Finally, no specioc assumptions have been made on Bob's behaviour concerning his computer security. We considered for our experiments that Bob was an average user with general knowledge in computer security. Current research are dealing with "paranoid" users.
Virus V1 is designed to be a very small virus (a few hundred bits to less that two kilobytes according to the settings) whose polymorphic and stealth capabilities are managed by virus V2 as described in Section 4. Here precisely lies the interest to use couple of viruses. First infection step is bound to remain undetected if V1 is small enough. Thus most of its functionalities (polymorphism in particular) are insured by V2 as described in section 4. Its characteristics, structure and functions here follow:
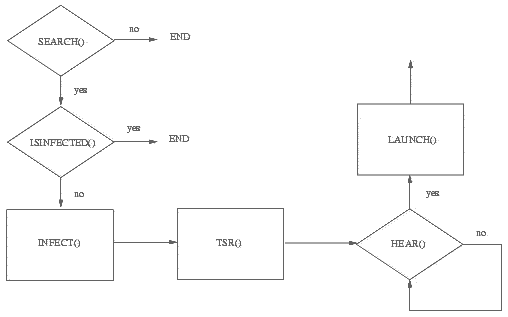
Figure 1: Virus V1 organization chart
From a technical point of view, V1 has an isinfected() routine to check whether the host computer is already infected or not (it is worth noticing that this routine is able to detect not only the current version of V1 but all the polymorphic version of this virus, since the attacker knows how to produce polymorphic versions from a previous one) and an infect() routine looks for specioc files and infects them. Finally a tsr() routine makes it resident and introduces (limited) stealth capabilities (in particuliar CTRL-ALT-DEL or PS -AUX commands must not show V1 process).
Figure 1 summarises V1 structure.
Virus V2 beneots from V1 action. Thus whilst this latter is a very small in size, V2 is larger and exhibits more complex functionalities and structure. Here precisely lies the interest and power of combined viruses. In turn, V2 complements V1 action by ensuring the complex stealth and polymorphic nature to V1. This is done essentially by turning V1 into a dormant state during V2's life in Bob's computer and modifying its code before waking it up. Another possibility is to really disinfect V1 form Bob's computer and to reinfect it by a modioed form of this orst virus. We developed two main variants of virus V2. The orst one aims to attack
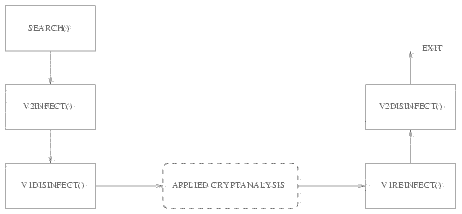
Figure 2: Virus V2 organization chart (infection part)
only one target cryptosystem. The second is able to treat several target cipher systems in a row. Without loss of generality here is a presentation of the orst variant.
The action of virus V2 allows powerful polymorphism of V1 and V2 itself. Once again only binary viruses are able to perform this to such a high level. Figure 2 summarises V2 structure.
We will not concentrates too much on computer attack since we primarily are interested in applied cryptanalysis. However, attacks with binary viruses in a purely computer security problem are fully and easily adaptable. We performed experiments where virus V2 was a home-made Trojan horse (for LAN or WAN attack context). Ultimately in each experiment, we took complete control of the target computer, surrendering it up to the attacker without being detected by current antivirus softwares.
Note that in this case, it may be not possible to attach virus V2 to a ciphertext (since the target computer owner may not use encryption at all). Thus it may be necessary to attach the virus to another kind of file. Fortunately this does not change the effciency of the attack (see Section 6 for the other solutions).
Whilst remaining general overall, we shall now focus on the version we developed for when only one cryptosystem is present in the target computer. In the case of several cryptosystems attacked in a row, action and disinfection of V2 occur according to the attacker's aim. Thus, the structure is just more complex but essentially the same.
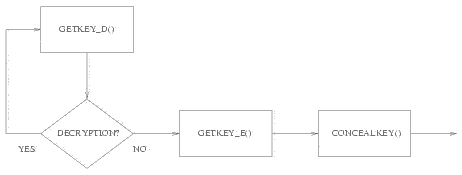
Figure 3: Virus V2 organization chart (applied cryptanalysis part)
For this part, structure of V2 is very specioc to the nature of cryptosystem binaries S. Indeed it must infect it in such a way that V2 is able to temporarily pass control to S during its own action and before deonitively abondoning control to it. Another very powerful way is to hook Windows API. Thus parameters (notably the secret keys themselves) of the different routines can be effciently eavesdropped.
During each next decryption process the caught key is compared to previously stored keys. When different, a counter is incremented and new key is stored in the same way. V2 then returns control to cryptosystem executable S. Note that infection occurs in such a way that key catching takes place at a very low level in the cryptosystem binary code in order to always have access to the plain secret key, not an encrypted version of it. Macro viruses like Caligula [20] made the mistake of stealing the key in an encrypted form.
Suitable executable infection and low level action is a far more effcient approach than simple keyboard buffer eavesdropping such as in (in so far information is available) Magic Lantern technology. The latter can easily be bypassed by not inserting secret keys via the keyboard (other possible solutions being the use of removable disk, "key gun" connected to a physical external port such as e-keys, smart cards,...).
The attack is completed. Figure 3 summarizes this scheme.
Remark.- Note that this attack is easily adaptable to public key cryptosystems. The crucial point is to infect the executable in such a way that V2 can access the unencrypted secret key during the computing. Only the key escape itself can be slightly different in some way. Charlie then intercepts the ciphertext sent to ALice by Bob and extract all the secret keys that are hidden in it.
When considering protection against these attacks, the game seems to be rather in the attacker's favour. As a general rule in computer security, computer protection is nearly almost condemned to reaction, at least for the very great majority of systems. The human ability to adapt and the unbounded imagination of the attackers make such attacks generally unlikely to be forecastable and thus prevented in advance.
From the general intrusion detection (ID) point of view, it is clear that things are very diffcult. Securing computers when dealing with the huge "number of rampant vulnerabilities in commonly used software" [14] and with the persistent lack of user's public awareness of basic computer security (even in sensitive areas like Defence) it is like trying to square the circle.
To protect against the family of attacks we presented in this paper, what are the possible different levels of action?
Our different experiments have been proven effective at fooling and bypassing all recent antiviral protection (Even when integrity checking or code emulation are used as part of the AV techniques.) we used both for V1 and V2. We consider that state-of-the-art antivirus programming cannot afford more than hindsight, especially against unknown polymorphic capabilities. Moreover the reverse-engineering of AVs will always yield enough useful information on how they work and how to fool them.
Currently we still have not found any satisfactory, generic solution to this problem but research is under way to build one.
This kind of attack have been proven dramatically effcient. Beyond the intrincic power of computer viruses (and especially the combined viruses), the clever use of cryptologic techniques considerably helped us to make our viruses very stealthy, polymorphic and compact.
A large and interesting field of research is to be considered in the future when considering the links between viruses (and more generally malwares) and cryptology.
This paper is dedicated to Kim Clancy and Mark Ludwig.
Unite de recherche INRIA Lorraine, Technopole de Nancy-Brabois, Campus scientifique,
615 rue du Jardin Botanique, BP 101, 54600 VILLERS LES NANCY
Unite de recherche INRIA Rennes, Irisa, Campus universitaire de Beaulieu, 35042 RENNES Cedex Unite de recherche INRIA Rhone-Alpes, 655, avenue de l'Europe, 38330 MONTBONNOT ST MARTIN Unite de recherche INRIA Rocquencourt, Domaine de Voluceau, Rocquencourt, BP 105, 78153 LE CHESNAY Cedex Unite de recherche INRIA Sophia-Antipolis, 2004 route des Lucioles, BP 93, 06902 SOPHIA-ANTIPOLIS Cedex
Editeur
INRIA, Domaine de Voluceau, Rocquencourt, BP 105, 78153 LE CHESNAY Cedex (France) http://www.inria.fr
1 Symbol || denotes text or string concatenation
2 One may find that this constitutes a very unlikely hypothesis, since one can estimate that generally users are very careful of their computer security. In fact, this belief is false. Real-life experiments we conducted actually showed that it is always easy to infect someone's computer, whatever may be the user. Social engineering provides a lot of tools and tricks that make infection really easy, maybe too easy.
[Back to index] [Comments (0)]