Justin Balthrop, Stephanie Forrest, M. Newman, Matthew Williamson
SCIENCE VOL 304 23 APRIL 2004 pp.527-529
April 2004
J. Balthrop and S. Forrest are in the Department of Computer Science, University of New Mexico, Albuquerque, NM 87131, USA; S. Forrest is also at the Santa Fe Institute, Santa Fe, NM 87505, USA. M. E. J. Newman is in the Department of Physics and Center for the Study of Complex Systems, University of Michigan, Ann Arbor, MI 48109, USA. M. M. Williamson is at HP Laboratories Bristol, Filton Road, Stoke Gifford, Bristol BS34 8QZ, UK. E-mail: forrest @cs.unm.edu
Computer viruses and worms are an increasing problem throughout the world. By some estimates 2003 was the worst year yet: Viruses halted or hindered operations at numerous businesses and other organizations, disrupted cashdispensing machines, delayed airline flights, and even affected emergency call centers. The Sobig virus alone is said to have caused more than $30 billion in damage (1). And most experts agree that the damage could easily have been much worse. For example, Staniford et al. describe a worm that could infect the entire Internet in about 30 s (2). A worm of this scale and speed could bring the entire network to a halt, or worse.
The term virus refers to malicious software that requires help from computer users to spread to other computers. E-mail viruses, for instance, require someone to read an e-mail message or open an attached f ile in order to spread. The term worm refers to infections that spread without user intervention. Because they spread unaided, worms can often spread much faster than viruses. Computer infections such as viruses and worms spread over networks of contacts between computers, with different types of networks being exploited by different types of infections. The structure of contact networks affects the rate and extent of spreading of computer infections, just as it does for human diseases (3-7); understanding this structure is thus a key element in the control of infection.
Both traditional and network-based epidemiological models have been applied to computer contagion (3-5). Recent work has emphasized the effects of a network's degree distribution. A network consists of nodes or vertices connected by lines or edges, and the number of edges connected to a vertex is called its degree. Of particular interest are scale-free networks, in which the degree distribution follows a power law, where the fraction pk of vertices with degree k falls off with increasing k as k-α for some constant α. This structure has been reported for several technological networks, including the Internet (8) and the World Wide Web (9, 10).
Infections spreading over scale-free networks are highly resilient to control strategies based on randomly vaccinating or otherwise disabling vertices. This is bad news for traditional computer virus prevention efforts, which use roughly this strategy. On the other hand, targeted vaccination, in which one immunizes the highest degree vertices, can be very effective (11, 12). These results rely crucially on the assumption that the degree distribution follows a power law, and also that the contact pattern is static.
Many technological networks relevant to the spread of viruses, however, are not scale-free. Vaccination strategies focusing on highly connected network nodes are unlikely to be effective in such cases. Furthermore, network topology is not necessarily constant. In many cases the topology depends on the replication mechanism used by a virus and can be manipulated by virus writers to circumvent particular control strategies that we attempt. If, for instance, targeted vaccination strategies were found to be effective against vir uses spreading over scale-free networks, viruses might be rewritten so as to change the str ucture of the network to some non-scale-free form instead.
To make these ideas more concrete, we consider four illustrative networks, each of which is vulnerable to attack: (A) the network of possible connections between computers using the Internet Protocol (IP), (B) a network of shared administrator accounts for desktop computers, (C) a network of e-mail address books, and (D) a network of e-mail messages passed between users.
In network A, each computer has a 32bit IP address and there is a routing infrastructure that supports communication between any two addresses. We consider the network in which the nodes are IP addresses and two nodes are connected if communication is possible between the corresponding computers. Many epidemics spread over such an IP network. Notable examples include the Nimda and SQLSlammer worms.
Network B is a product of the common operating system feature that allows computer system administrators to read and write data on the disks of networked machines. Some wor ms, including Nimda and Bugbear, can spread by copying themselves from disk to disk over this network.
Network C has nodes representing users and a connection from user i to user j if j's e-mail address appears in i's address book. Many e-mail viruses use address books to spread (for example, ILoveYou). A closely related network is network D, in which the nodes represent computer users, and two users are connected if they have recently exchanged e-mail. Viruses such as Klez spread over this network.
Degree distributions have been measured for examples of each of the four networks (see the f igure). In network A, all ver tices have the same deg ree, so the distribution has a single peak at this value (blue histog ram). In network B, the distribution consists of four discrete peaks, presumably cor responding to different classes of computers, administrators, or administration strategies (red histogram).
The two e-mail networks have more continuous distributions and are shown as cumulative histograms. Although neither network has a power-law degree distribution, both have moderately long tails, which suggests that targeted vaccination strategies might be effective. However, calculations show that for network C, about 10% of the highest degree nodes would need to be vaccinated to prevent an epidemic from spreading (7), whereas network D would require about 80%. The f irst of these f igures is probably too high for an effective targeted vaccination strategy, and the second is clearly f ar too high. (Targeted vaccination would be entirely ineffective in the other two networks as well, because the nodes are much more highly connected.)
The two e-mail networks illustrate the ways in which different virus replication strategies can lead to different network topologies. An e-mail virus could look for addresses in address books, thereby spreading over a network with a topology like that of network C, or it could search through other f iles or folders on the machine for addresses of senders and recipients of archived e-mail messages, giving a topology more like network D. Another example is provided by the Nimda virus, which infects Web servers by targeting random IP addresses, producing a network like network A. However, if the virus had a more intelligent way of selecting IP addresses to attack (e.g., by inspecting hyperlinks), then it might spread over a topology more like that of the Web, which is believed to have a power-law degree distribution (9, 10).
A control strategy is needed that is immune to changes in network topology and that does not require us to know the mechanisms of infections before an outbreak. A number of methods have been proposed (13). One such strategy is throttling, f irst introduced for the control of misbehaving programs (14) and recently extended to computer network connections (15). In this context, throttling limits the number of new connections a computer can make to other machines in a given time period. Because it works by limiting spreading rates rather than stopping spread altogether, the method does not completely eliminate infections but only slows them down. Frequently, however, this is all that is necessary to render a virus harmless or easily controllable by other means (16).
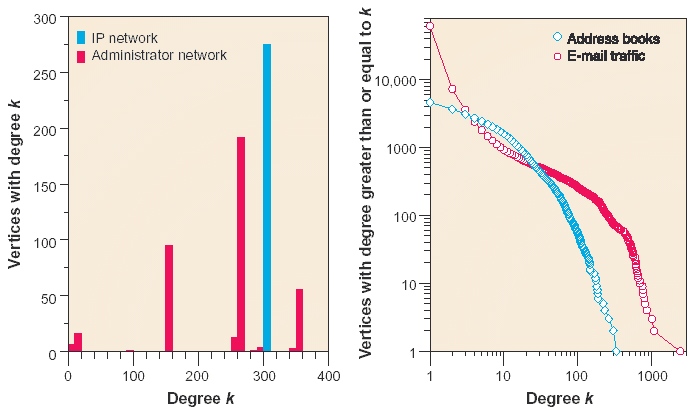
Infectious connections. (Left) Degree distributions for the IP (blue) and administrator (red) networks. The administrator network data were collected on a system of 518 users of 382 machines at a large corporation. Computers in this network are connected if any user has administrative privileges on both computers. (Right) Cumulative degree distributions for the e-mail address book (blue) and e-mail traffic (red) networks. The e-mail address book data were collected from a large university (7). The e-mail traffic data were collected for complete e-mail activity of a large corporate department over a 4-month period (18).
Throttling is most effective when viruses generate traff ic at a rate signif icantly higher than normal network communications. Luckily this is true for many common protocols and the viruses that exploit them (15, 17). For a virus to spread, it needs to propagate itself to many different machines; to spread quickly, it must do so at a high rate. For example, the Nimda worm attempts to infect Web servers at a rate of around 400 new machines per second, which greatly exceeds the normal rate of connections to new Web servers of about one per second or slower (15).
A throttling mechanism that limited connections to new Web ser vers to about one per second would slow Nimda by a factor of 400 without affecting typical legitimate traff ic. This could easily be enough to change a serious infection into a minor annoyance, which could then be eliminated by traditional means. Slowing the spread of Nimda by a factor of 400 (from a day to more than a year) would have allowed plenty of time to develop and deploy signatures and prophylactic software patches. (Of course, if throttling were implemented on only a subset of the nodes in a network, then infections could spread more easily.) In addition to reducing vir us spread, throttling has the practical benef it of reducing the amount of traff ic generated by an epidemic, thus reducing demand on networking equipment--often the primar y symptom of an attack.
Targeted vaccination strategies for the control of computer viruses are unlikely to be generally effective because the networks over which viruses spread are not suff iciently dominated by highly connected nodes, and because network topology can be influenced strongly by the way in which a virus is written. Throttling provides a promising alternative strategy that works with any network topology and can greatly reduce viruses' impact by slowing their spread to the point where they can be treated by conventional means. The disparity between the speed of computer attacks (machine and network speed) and the speed of manual response (human speed) has increased in recent years. If this trend continues, automated mechanisms like throttling will likely become an essential tool, complementing the largely manual approach of software patching in use today. The idea of rate limits is not specif ic to viruses, and could be applied to many situations in which an attack or cascading failure occurs faster than possible human response.